
Modern Workplace Requires a Secure Digital Twin
TL; DR
- The Modern Workplace is a model for the future of digital work
- A digital twin is a virtual representation of a virtual or physical asset
- Creating a security model as a digital twin of the Modern Workplace will help accelerate user adoption
- The future of work is mobile where a secure digital twin can help align expectations
- New threats, like Pegasus, require new solutions to understand a security posture before they impact business
- SASE (secure access service edge) companies like Lookout are accelerating solutions for mobile, identity, and cloud
What's in a Name?
These days it can go by many names, but users of technology have fundamentally evolved to a multi-device, multi-app approach for accessing their data and information:
- Digital workspace
- Virtual office
- Virtual Desktop
- Virtual Apps
- Cloud Desktop
- Etc.
To quote one of the leader's in the user technology space, Microsoft classifies this as the Modern Workplace:
The nature of work has changed. Employees expect to work securely from anywhere, on any device, and they put a high premium on work that enriches and fulfills them. When their productivity tools enhance the quality and effectiveness of their work experience, they’re happier, more valuable, and more likely to stay.
My career grew during the time when even the idea of a unified digital ecosystem was in its infancy. iPhones were only a couple of years old, and we were still struggling to get native Microsoft Exchange support (did I show my age here?).

The Rise of the Digital User Security
Today, news feeds are filled with examples of how digital security has impacted the Modern Workplace. What was an ad tracking plugin in Internet Explorer 10 years ago which simply created ad revenue (Gator anyone?), is now a highly potent, highly focused, revenue machine for exploitation using ransomware, phishing, and data exploitation.
COVID-19 only accelerated this trend as overnight, a deluge of office users moved to a hybrid or permanent work-from-anywhere situation. And let's think about it: How must you secure remote users and devices on the network edge? What about when they roam back into the office or secure network? It's very tough, and there are some security terms everyone should be familiar with that align with this posture:
Zero-Trust
The vetting and analysis of a user to understand their risk before accessing data or applications.
VPN
A virtual private network (VPN) or also conceived as an encrypted tunnel through the internet to a secured network to use a set of data or applications.
Advanced Persistent Threats(ADT)
A malicious person or group with resources and expertise focused on multiple ways to digitally attack and secure a foothold on a person or company for exploitation.
Bad Actor
The person or people behind an ADT whose goal is criminal activity
Phishing
A facet of social engineering (i.e. getting digital access without brute force by impersonating a user) where fraudulent, fake asks or links are sent to someone which then allows a bad actor digital access using impersonation.
Zero-Day
A vulnerable piece of software code that may or may not have a fix.
Education about the current landscape of how users are targeted, the jargon used to describe this, and ways to avoid or mitigate these is a top priority for security professionals.

Post-pandemic, mobile users and devices will become the standard for digital workplace access, not just an exception. Try and think about all the different products and functions built into your devices to enable secure access...just kidding, you don't know them all! Today, that's by design. This is the continual evolution of a secure user experience; or, to put it blunter, how to keep a user secure without them interacting, managing, or having to know what's required to keep them, and you, secure.
Try and think about all the different products and functions built into your devices to enable secure access...just kidding, you don't know them all!
A Secure Modern Workplace Starts with a Digital Twin
As technology is further integrated with our day-to-day lives, it's necessary to attempt to model both the virtual and the physical worlds. As the Modern Workplace has matured and is constantly transforming through forced acceleration (i.e. COVID), there is a need to create a 'twin' or replica of this workplace through security.

A digital twin for a secure Modern Workplace will help benefit an organization in a few ways:
Alignment of User Experience
Always at the top of technology leaders' lists but never typically defined, user experience is more a journey than a destination. Security adds another complex layer that can typically modify or destroy a vetted UX (user experience) within seconds.
New technologies like UBA (user behavior analytics) mixed with machine learning allow security systems to learn and apply context to a user's digital pattern over time, but typically those are real-time and clumsy at first. Having a goal of a user experience that's both secure and delightful is now a talent differentiator.
Having a goal of a user experience that's both secure and delightful is now a talent differentiator.
Discovering User Workflows
Most organizations know that the workflow of a user in accounting versus an IT user is very different, yet don't take the time to understand why. The solutions they implement are also undifferentiated outside of a couple of tweaks like not to scan a directory here, or allow a user over there. It's pretty basic.
A secure Modern Workplace digital twin for a role or department would build a persona that could be quickly applied and modified enhancing the visibility of an organization. A department's goals and evolution could also be tested as a company grows allowing technology to conform to a more granular user group.
Increase User Acceptance, Remove Operational Bottlenecks
How often has a great technology idea or initiative, once implemented, fallen flat when rolled out to a user community? I'd wager security's track record is far worse, save one key ideal that acts like a get-out-of-jail-free card: "It's security-related, sorry!"
Software-as-a-service, mobile devices, and work-from-anywhere have all contributed to shadow IT (users finding solutions outside the 'approved' technology stack) as technology decisions aren't fully aligned to user expectations.
Again, using a secure Modern Workplace digital twin, pilot user groups can help drive this sentiment. This also rolls into user experience and workflows where user acceptance ensures organizational champions are created who then help their peers while strengthening their company loyalty.
As a byproduct, a secure digital twin would also remove operational bottlenecks as situations, exceptions, policies, and alignment could all be determined before rolling out to the organization as a whole.

The Future is Mobile
I've now worked remotely for over 6 years. The transition from office to anywhere was not easy. It took me solid 12 months to reset how I worked. Many of us are now in that timeframe where remote is just another day at the office. You can be productive, balance the things around you, and contribute. And many don't want to go back, at least full-time.
Companies with physical offices are revamping their in-person spaces for:
- Less open space
- Less shared hardware
- A larger focus on transient workers than dedicated desks
- Overall, more 'hotel' like
- Users come in part-time, collab safely, work in a secluded space, and then go back home/remote
- That space is then sanitized and reset
- The user probably has a laptop and a phone at a minimum assigned to them

This also creates larger challenges where in previous situations these were only 'exceptions':
Data Governance
Which data is critical for a user to have access to? Which is not? Is there any data that should never be accessed?
Application Alignment
What applications does a particular role require? What if that application is compromised? Can a user leverage that application to get unauthorized access to other resources?
Hybrid Remote
This one seems obvious, but before the pandemic, there were clear rules and delineations for these types of employees. In the new era of Hybrid work, a new designation will have to be created along with new rules. This includes new solutions, software, and policies.
A secure digital twin could help accelerate these scenarios while being inclusive of the users who will use them. An included human is a responsive human, and for cyber security, that's invaluable.
An included human is a responsive human, and in security, that's invaluable.
New World, New Threats, New Solutions
As COVID-19 battles on, the inevitable is happening: We're quickly adapting. As humans, partners, or employees. Solutions in the marketplace are also becoming more innovative. This also means the bad guys are evolving as well.
One critical example of how security has dominated the pandemic landscape is Pegasus.
Discovered in 2016 by Lookout, NSO's Pegasus exploits multiple zero-day vulnerabilities (called Trident) on an iPhone (fixed before iOS 10 came out; for perspective, Apple is about to release iOS 15). Even an iOS upgrade and patch cannot remove it once it's installed and the device must be completely wiped and not restored from backup. Pegasus has also since evolved.
Originally designed for law enforcement organizations and vetted customers, Pegasus can do things like:
... extract highly accurate GPS coordinates, photos, email files and encrypted messages from apps such as WhatsApp and Signal. It can also turn on the devices’ microphone to eavesdrop on private in-room conversations or phone calls and activate the camera to record video.
Because the malware is at the root level of a device (called 'rooted'), regardless of encryption level, it can analyze whatever the user sees. You and I don't see encrypted strings, but human-readable apps and data. Pegasus would see the same and be able to send this information back to its command-and-control.

Pegasus' focus has been business executives, human rights activists, journalists, academics, and government officials and not the typical person like you or me, but the fact that this software is actively being used is reason to be concerned.
Lookout, a mobile-derived SASE (Secure access service edge) company, was not only a discoverer of Pegasus, they're also a solution for it. Their ecosystem is compromised of three core foci organized in the picture below as a 'choose-your-own security posture experience using one or all of their solutions:
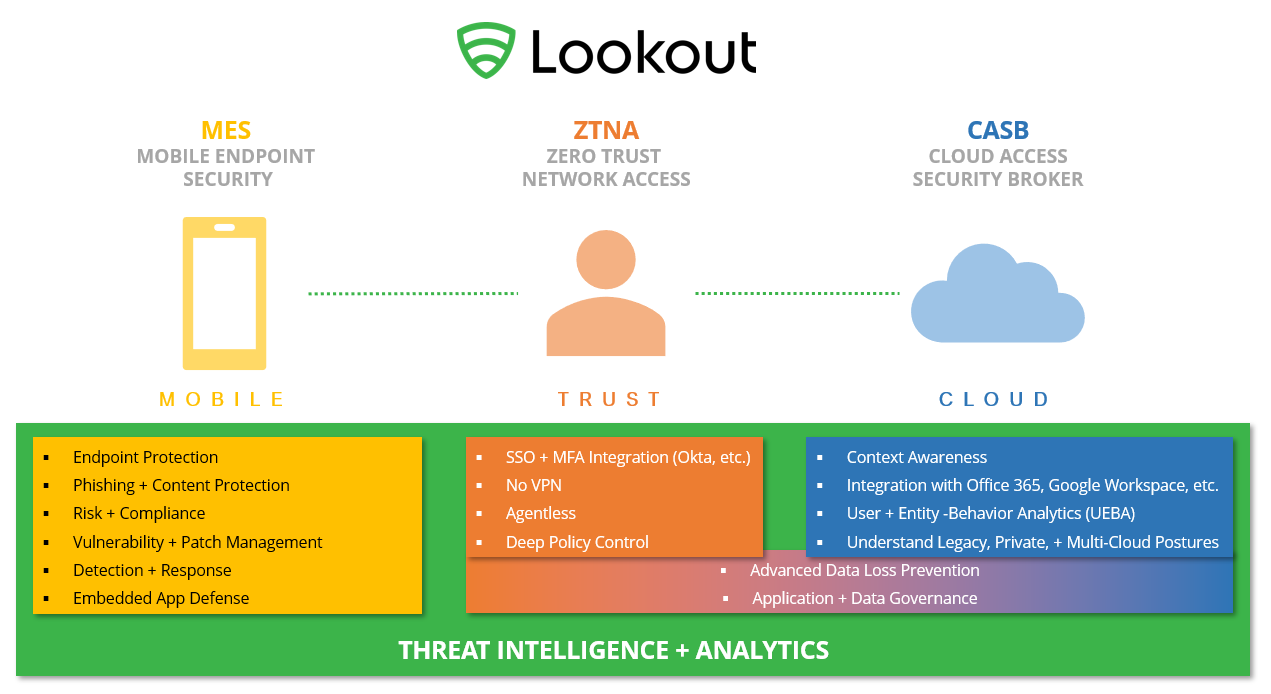
Using device analytics aligned to user behavior, file system changes, and network traffic, Lookout can detect and understand even zero-day threats like Pegasus.
While a comprehensive secure digital twin may not exist for every situation in the modern workplace, always looking towards a more user-centric posture will always pay dividends.
